-
 System CertificationZOHOCERT establishes trust with excellent quality, conveys trust with the concept of Zhongzheng, and enhances customers' ability to respond to risks and...
System CertificationZOHOCERT establishes trust with excellent quality, conveys trust with the concept of Zhongzheng, and enhances customers' ability to respond to risks and... -
 Product CertificationZOHOCERT establishes trust with excellent quality, conveys trust with the concept of Zhongzheng, and enhances customers' ability to respond to risks and...
Product CertificationZOHOCERT establishes trust with excellent quality, conveys trust with the concept of Zhongzheng, and enhances customers' ability to respond to risks and...
-
 Public DocumentsZOHOCERT establishes trust with excellent quality, conveys trust with the concept of Zhongzheng, and enhances customers' ability to respond to risks and challenges, as well as their sustained commercial value, to win trust!
Public DocumentsZOHOCERT establishes trust with excellent quality, conveys trust with the concept of Zhongzheng, and enhances customers' ability to respond to risks and challenges, as well as their sustained commercial value, to win trust! -
 Case PresentationZOHOCERT establishes trust with excellent quality, conveys trust with the concept of Zhongzheng, and...
Case PresentationZOHOCERT establishes trust with excellent quality, conveys trust with the concept of Zhongzheng, and...


Certification Description
■ISO27040 Data Storage Security Management System Certification
ISO 27040 standard is designed to help purchasers and users of computer storage technology identify and address the associated information risks, covering the security of devices and media, the security of management activities related to devices and media, applications/services and end users, and the security of information transmitted over communication links associated with the storage.
ISO 27040 standard provides detailed technical guidance on how organizations can define appropriate levels of risk mitigation and is one of the highest performing standards for managing data storage security.
ISO 27040 standard also defines and broadens the boundaries of storage security, including not only storage methods, transmission methods, and browsing rights, but also laws and regulations, personnel management, material management, etc., covering the security of equipment and media, and equipment and media. The security of related management activities, the security of applications and services, as well as the safety aspects related to the end user during the service life of the equipment and media and after the end of use.
■ISO27040 Certification Process
1. Pre-assessment (optional)
2. Submit an application for certification
3. Sign the certification contract
4. Certification site audit
5. Issue certificates
6. Annual supervision and audit
■Certification Standards
ISO 27040: 2015 Information technology - Security techniques - Storage security
■ZOHOCERT
Is a professional service organization that has been deeply involved in the IT information industry for many years.
Has a number of senior academic management experts with more than 20 years of practical experience.
Scope of Certification
Certification Scheme
1 Scope of application
This certification scheme is applicable to Fangyuan Mark Certification Group Co., Ltd. (hereinafter referred to as: ZOHO) to implement data security risk management certification, to meet the requirements of the third-party certification system, as a standard for providing certification services. If necessary, the relevant technical requirements shall be supplemented in the certification contract. This certification scheme shall be confirmed and adopted when the two parties sign the contract.
2 Authentication Mode
ZOHO first conducts an initial audit of the auditees' data security risk management, and after assessment, confirms whether the certification is approved; after passing the certification, it supervises the certified customer within the validity period of the certification certificate to confirm whether the certification requirements are continuously met.
3 Certification Process Flow Chart
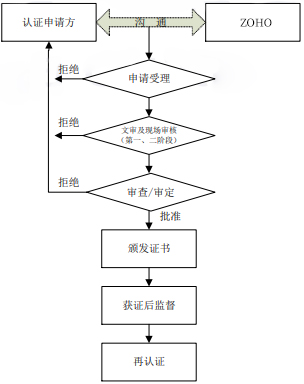
4 Application for Certification
4.1 certification applications
a. Certified customers have a clear legal status, customers have a business license, institution legal person certificate, social organization registration certificate, non-enterprise legal person registration certificate, etc., can independently apply for certification. Other types of customers should be applied by qualified units;
b. When required by the state, local or industry, the certification client shall have the prescribed administrative license documents, and the scope of application for certification shall be within the scope approved by the legal status documents and administrative license documents;
c. Certification customers promise to comply with the laws, regulations and other requirements of the country, promise to always comply with the relevant provisions of certification, bear the legal responsibilities related to certification, and have the obligation to assist the supervision and inspection of certification regulatory authorities, and provide relevant materials and information truthfully for inquiries and investigations of relevant matters;
d. Certified customers are not included in the "list of serious illegal enterprises" in the national enterprise credit information publicity system ";
e. Pass the data security risk assessment test and provide the test report within the past year;
f. The certification customer promises to use the certification certificate, certification mark and related information after obtaining ZOHO certification, and shall not use the words and symbols of the data security risk management certification certificate to mislead the public that its products or services have passed the certification and pay the certification fee according to the contract, and accept supervision according to the regulations;
g. Certification The customer undertakes to inform ZOHO of the information of data security risk management changes and other matters that may affect the ability of data security risk management to continuously meet the requirements of certification standards according to ZOHO requirements after obtaining ZOHO certification, generally including: the customer and relevant parties have major complaints; Major accidents occur; Changes in relevant conditions (including: changes in legal status, production and operation status, organizational status or ownership, compulsory certification or other qualification certificates; changes in legal representative, top management, and management representative; changes in the workplace of production, operation or service; changes in the scope of activities covered by data security risk management; major changes in data security risk management and important processes, etc.); other important situations affecting the operation of data security risk management occur;
h. During the certification audit, the certification client can provide activities or processes related to the scope of the proposed certification.
4.2 does not accept the application for certification
a. The scope of certification applied by the certification client exceeds the scope approved by the legal status document and the administrative recognition document;
b. certification customers do not meet other relevant requirements in the 4.1 or other violations of national laws and regulations, industry regulations within the past year.
5 Audit Implementation
5.1 Audit Guidelines
certification parties are as follows:
ZOHO/S-RZ-ZY-21-001 "Data Security Risk Management Requirements" audit guidelines also include the auditees' applicable policies, procedures, standards, laws and regulations, data security risk management requirements, contract requirements or industry specifications. When the above standards are updated, the updated version is used.
5.2 audit process
5.2.1 Initial certification audit
The purpose of the initial certification audit is to evaluate the implementation of data security risk management of the certification organization. The audit team comprehensively evaluates whether the certification organization meets the standard requirements and related requirements and whether the operation is effective by collecting objective evidence.
initial certification audit specific concerns:
a. The effectiveness and control methods of the data security risk management process specified by the auditee;
b. Self-assessment and self-improvement implementation, etc.
5.2.2 Monitoring activities
5.2.2.1 Mold of oversight activities
supervision activities include supervision audit and daily monitoring. Main contents of supervision and audit:
a. Significant changes related to the organization's data security risk management since the last audit (e. g., resources, processes, organizational structure, identified critical control points, etc.);
b. Ongoing operational control of the achievement of data security management objectives;
c. Verification of the improvement of the issues raised in the previous audit;
d. Self-assessment and self-improvement implementation, etc.
5.2.2.3 Frequency of supervision and audit
During the validity period of the certificate, the certified customer shall be subject to a supervisory audit, which shall be conducted at least once every calendar year (except for the year in which recertification is due). The first supervisory audit after the initial review/recertification shall be conducted within 12 months from the date of the certification decision; thereafter, the supervisory audit shall be conducted at least once every calendar year (except the year in which recertification is to be conducted), and the time interval between the two supervisory audits shall not exceed 15 months.
If the certification certificate is suspended due to the failure of the certified customer to carry out the supervision audit within the specified time, after the resumption of the supervision audit, the next audit time shall be calculated according to the originally planned time.
5.2.3 Main contents of recertification and recertification audit:
a. the continued effectiveness of the organization's data security risk management in the previous certification cycle;
b. The impact of important changes related to data security risk management on data security risk management;
c. The achievement of data security risk management objectives;
d. Verification of the improvement of the issues raised in the previous audit; Self-assessment and implementation of self-improvement, etc.
5.3
audit team shall communicate with the audited party before the on-site audit to confirm the audit arrangement and explain the agenda of the first and last meetings. The audit team conducts the audit in accordance with the schedule in the audit plan, and collects and verifies relevant information on a sample basis through appropriate methods such as consulting the documents and records of the audited party, interviewing with the personnel in the process and activities, observing the product and service formation process and activities, forming audit findings and confirming non-conformities.
During the audit process, the audit team communicates with the audited party in a timely manner, informs the audit process, confirms the audit evidence, and resolves differences. When the audit findings indicate that the purpose of the audit cannot be achieved, the reasons shall be explained and follow-up measures shall be agreed. If it is necessary to change the purpose and scope of the audit or terminate the audit, it shall be implemented after review and approval by the audit dispatching agency. Before the end of the on-site audit, the audit team leader shall communicate the information of the on-site audit with the audited party, and the audit team shall prepare the audit report and submit it to the audited party.
the audit report belongs to ZOHO, if there is any change in the audit follow-up activities (including ZOHO's certification decision period), ZOHO will provide the audit report to the audited party again. The audited party is requested to properly keep the audit report and other corresponding materials.
Certification Fees
Certificate Sample